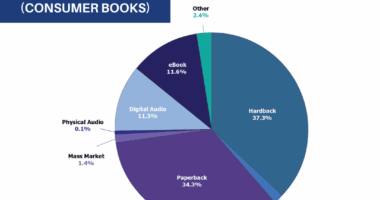
At the 23rd USENIX Security Symposium last week in San Diego, California, a new-style of Android security threat was discussed: user interface inference. This next-generation of attack technique communicates the state of any targeted application –the most intimidating example may be if malware can detect that a user has clicked a login button. Knowing that this behaviour usually results in a username and password being entered, a fake dialog box could be thrown up in front of the user to gather those details.
To be effective, the attack application has to be running in the background. The trick to getting these applications past users is to piggyback on other tasks so that they are more difficult to notice.
It will come as little comfort, but Android isn’t the only platform vulnerable to this kind of attack. Researchers have indicated that this type of exploit could be generalizable, making its way to other major operating systems, including: MacOS X, iOS, and Windows.
Detecting the presence of these UI inference attack apps is difficult, because they aren’t exploiting particular operating system vulnerabilities (also making them difficult to patch or protect against). The best defence is to remain aware: pay attention to unusual device behaviours such as a battery that drains much faster than usual or much slower hardware performance (both of which may indicate that additional processes are running).