There have been a number of critical vulnerabilities discovered on the entire Amazon Kindle line of e-readers. The attacks could give hackers access to your entire device. Amazon has issued a patch to close all of the loopholes and everyone is encouraged to download the 5.13.4. firmware update right away, even people who have elected to root their device.
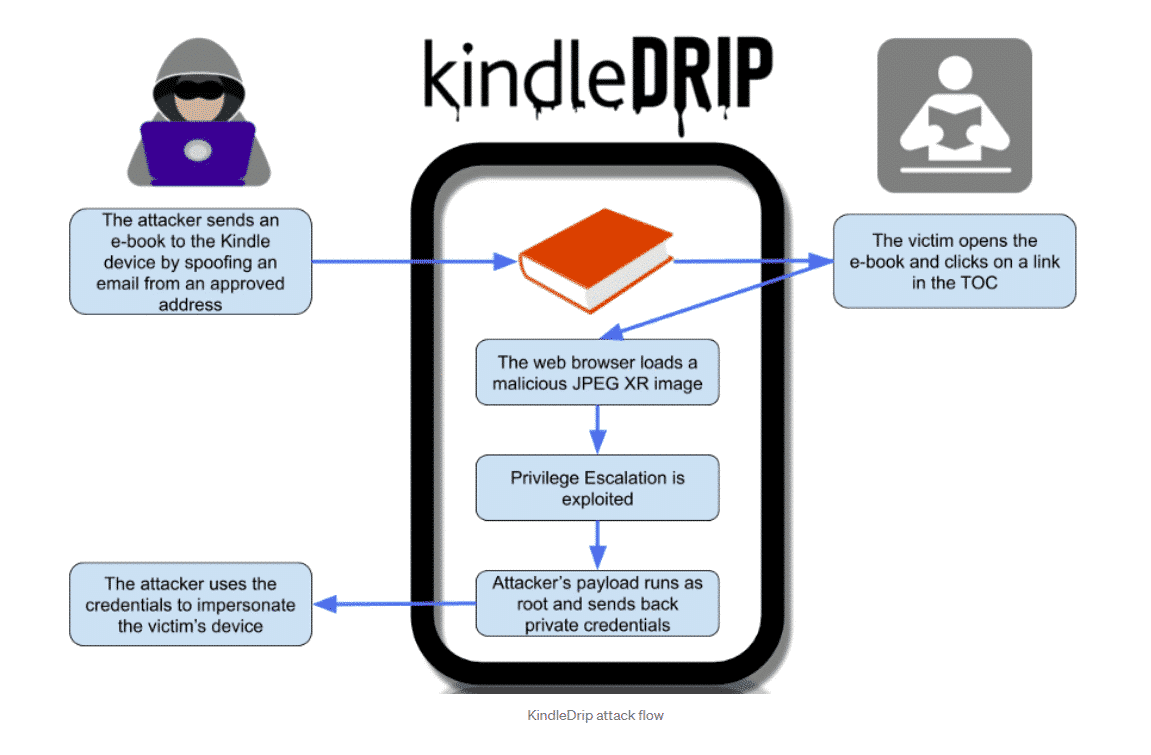
Researcher Yogev Bar-On, of Readlmode Labs, who discovered the now-patched issue, detailed in a blog post on how he was able to access a victim’s Amazon account simply by knowing their email address. The attack – dubbed ‘KindleDrip’ – relied on three vulnerabilities found in the e-reader. The first bug allowed a spoofed email address to bypass authentication checks, enabling a malicious e-book file to be sent to a victim’s device. Amazon’s ‘Send To Kindle’ feature gives users the option to send a purchase directly to their device using a list of pre-approved senders such as their Kindle email address, which is automatically generated by Amazon.
If you are not familiar with the program, send to Kindle is a system where you can email ebooks to your Kindle address from another email address. The Kindle email address belongs to your user account, when you register a Kindle and can be be viewed on your Amazon account. Why would you use this? Let’s say you are at work, and find a book online you want to read later on your Kindle, you can send an email to your Kindle email address from your work email address and the book will automatically appear on your Kindle when you connect to WIFI later on in the evening.
The second issue was a vulnerability in the way that the Kindle parses the image format JPEG XR, which can be loaded via a web browser. If the user clicks a link in the e-book, such as one in the table of contents, it will open a browser window that contains the malicious JPEG XR image. The image is parsed and runs arbitrary code under the context of a weak user.
A third vulnerability, a privilege escalation bug, is exploited and the attacker’s payload runs as root. Chained together, the three bugs could enable the attacker to achieve RCE and send back the private credentials to themselves.
Yogev Bar-On told Amazon about this problem is December and was awarded $18,000 in a bounty. Amazon has patched the file and issued a firmware update on December 10th, 2020. There are no other new updates since this one was pushed out, so it is critical you install it right away.
Michael Kozlowski is the editor-in-chief at Good e-Reader and has written about audiobooks and e-readers for the past fifteen years. Newspapers and websites such as the CBC, CNET, Engadget, Huffington Post and the New York Times have picked up his articles. He Lives in Vancouver, British Columbia, Canada.